Existing ways of combatting The Botnet - and why they're ineffective
VPNs
These are proxies that route ALL traffic (not just HTTP) through their servers. There are lots of them claiming to be 'no log', but it is easy to find examples where people got ratted out by these, like https://www.wipeyourdata.com/other-data-erasing/no-logs-earthvpn-user-arrested-after-police-finds-logs/ (archive). Even assuming the 'no log' policy is true, the government could still possibly legally force the provider to track someone (at least in certain countries where that's allowed). If that's not an option, there's always the old raid them and steal the servers (archive) (MozArchive) tactic. Of course, VPN traffic is also easily blocked at the ISP or website level.
VoIP, social, IM, etc.
Simply suffers from lack of usage - so if you want to actually reach anyone, it's Facebook, Skype, etc. Much of the commonly recommended "secure and private" IM software has various issues (Signal and Telegram require a phone number; Keybase has had a security audit which found many issues (local); Matrix protocol has just had a security issue found (archive)). TOR-based messengers rely on the security of the TOR network, which is analyzed below. Server-based ones, on the other hand, rely on the security of servers controlled by people you don't know. And as usual, it's all going through the enemy's networks. I don't mean to say that all those alternative ways of communication are useless, but that we can't rely on only one layer of protection - the messaging application level.
UPDATE August 2025: this is going to become very obvious soon with the resurrection of Chat Control (archive) (MozArchive), which I was planning to write about earlier, but then it died (archive) (MozArchive), and I was assuming (or maybe just hoping?) it'd stay dead. Not in this cursed world, apparently; the necromancers just can't stop animating their favorite corpse to haunt us all.
When talking about Chat Control, people almost always focus on the horror of breaking encryption, but if you read the actual law (local), you will realize that the problems with it go much deeper than that. For example, every hosting or communication provider will have to assess the risk that his service will contribute to the proliferation of child sexual abuse (and do that every year / 2 / 3 according to the risk level). There is a template for this at the end of the document. After that's done, the communication platform will have to perform risk mitigation
which consists of:
- adapting, through appropriate technical and operational measures and staffing, the provider’s content moderation or recommender systems, its decision-making processes, the operation or functionalities of the service, or the content or enforcement of its terms and conditions;
- reinforcing the provider’s internal processes or the internal supervision of the functioning of the service;
- initiating or adjusting cooperation, in accordance with competition law, with other providers of hosting services or providers of interpersonal communications services, public authorities, civil society organisations or, where applicable, entities awarded the status of trusted flaggers in accordance with Article 22 19 of Regulation (EU) 2022/2065 …/… [on a Single Market For Digital Services (Digital Services Act) and amending Directive 2000/31/EC];
- initiating or adjusting functionalities that enable users to notify online child sexual abuse to the provider through tools that are easily accessible and age- appropriate;
- initiating or adjusting functionalities that enable users to control what information about them is shared to other users and how other users may contact them, and introducing default suitable privacy settings for users who are children;
- initiating or adjusting functionalities that provide information to users about notification mechanisms and direct users to helplines and trusted organisations, where users detect material or conversations indicating potential online child sexual abuse;
- initiating or adjusting functionalities that allow the providers to collect statistical data to better assess the risks and the effectiveness of the mitigation prevention measures. This data shall not include any personal data.
In short, every communication platform (which would include tiny XMPP servers like mine) would need moderators and a ToS; reporting functionality; ability to change privacy settings and private defaults for children; links to helplines and trusted organizations
(wtf?); as well as collecting some kind of statistical data (the end of no-logs services like my MUC).
Do you see now how it's not just about breaking encryption? In fact, that's irrelevant now because the new version of Chat Control explicitly forbids that. But anyway, did something in the above paragraph catch your attention? Because, to implement the private defaults for children
part, you'd need to track their ages. And that is exactly what the EU requires:
Providers of interpersonal communications services that have identified, pursuant to the risk assessment conducted or updated in accordance with Article 3, a risk of use of their services for the purpose of the solicitation of children, shall take, the necessary age verification and age assessment measures to reliably identify child users on their services, enabling them to take the mitigation measures.
Anyway, after performing the risk assessment and mitigation you have to send the results of that to some coordinating authority
(these are per country). If they decide there is a high enough risk of child abuse proliferation, they will force you to install detection technologies
:
The Coordinating Authority of establishment shall have the power to request the competent judicial authority of the Member State that designated it or another independent administrative authority of that its Member State to issue a detection order requiring a provider of hosting services or a provider of interpersonal communications services that are classified as high risk in accordance with Article 5(2) or parts or components of the services classified as high risk that fall under the jurisdiction of that Member State to take the measures specified in Article 10 for the sole purpose of to detecting in visual content or URLs the dissemination of online child sexual abuse material on a specific service or parts or components of the service, classified as high risk in accordance with Article 5(2), for a limited period as specified in paragraph 9 of this Article.
A little later the gov-boomers expose their lack of familiarity with the relevant technology:
Providers of hosting services and providers of interpersonal communications services that have received a detection order shall execute it by installing and operating technologies approved by the Commission to detect the dissemination of known or new child sexual abuse material or the solicitation of children (the ‘technologies’), as applicable, using the corresponding indicators provided by the EU Centre in accordance with Article 46. In interpersonal communications services using end-to-end encryption, those technologies shall detect the dissemination of child sexual abuse material prior to its transmission.
Obviously - if you're running something like an XMPP server - the bolded is impossible. Gov boomers are assuming everything is like Discord or Signal, where the client and server are the same thing. So, they figure they don't have to care about compromising encryption because they will just grab the data client-side earlier. But, this approach can't be applied to XMPP as the person that controls the server, doesn't control the client. So even if they judge the server as dangerous, they will only be able to apply the general risk mitigation
requirements. Of course, this is still way too much burden for your average XMPP hoster, and will bury him. But at least XMPP servers are truly immune to having to decrypt their users' communications. Yet, can we be sure the spies won't go after XMPP clients on the software repos? After all, they also have a section called Obligations for software application stores
which says that those need to:
take reasonable measures to prevent child users from accessing the software applications in relation to which they have identified a significant risk of use of the service concerned for the purpose of the solicitation of children;
So yeah, software distributors will also have to verify ages. Either way, prepare to have your images scanned on any communication platform where the server and client are the same. And of course, if the users are not running E2EE, the spies can also enforce scanning server-side.
Is it not obvious by now, that we cannot fight the botnet just by installing "NanonChatAppSupreme"? We are now surrounded not only by the big corporations that want to collect our data for profit and lock us into their ecosystems (they are the only ways of communication most people know), but also by states (or multi-state hydras like the EU) that want to bury all alternative platforms with an avalanche of requirements that they cannot hope to fulfill. So, even if you managed to escape the big corpos and dragged your normie friends to XMPP, Matrix or whatever (and you trust your hosts), the second form of the final boss is waiting to devour you while you're out of items and on low HP. This seems very deliberate.
Oh, and if you think "ha-ha! I use [insert messenger that's independent of servers, or can switch them, etc], EU spies can't touch me, hahaha!" then hold it, because this isn't their only way to slither in. Again, if they get a clue in a few years, they could just force the software repositories to modify the binaries or even sources on github to perform client side scanning. They could install spyware on the target devices like they do with journalists already. And I'm sure I'm missing ways. By the way, the new law is a lot longer, but I don't care to even read all of it, as most of it doesn't seem relevant here. There's stuff about the communication provider having to release transparency reports about the results of child abuse investigations, etc. But that's just adding more requirements to an already buried service so...There's also a bit about how, if the service is hosted outside the EU and ignores pleas for cooperation, they will just block it. Either way, another proof the botnet is physical.
File sharing, hosting...
All regular hosting / file sharing providers have huge lists of what's allowed and what isn't. Even my current host reserves the right to suspend, block or cancel access to any and all Services
, if they decide something contradicts their list. And of course, copyright holders can claim something is violating theirs, and you get your shit deleted then. Rom sites have been getting taken down recently for example. There are also 'good hosts' like autistici.org, but who's to say the government won't eventually take them down if they host too much stuff they don't like? As long as we're using their networks, nothing is safe. Push comes to shove and they raid the servers. Even Freedom Hosting went down eventually.
Operating systems
Alternatives to Windows are available, but you will come across Microsoft's system sooner or later - whether at a relative's house, school (they have deals with those (archive) (MozArchive)), or somewhere else. Not that Linux is all that great either in the botnet department - big corporations like Mozilla or Red Hat (through systemd), still influence it in negative ways. This will happen in any society in which deals based on profit and / or control are prevalent.
The TOR Illusion
The TOR network allegedly allows you to browse the Internet anonymously. It works like 3 proxies connected together except encrypted, so a "proxy" (called the TOR node) cannot see the contents of the previous, only the destination. However, the last node does see unencrypted traffic - so we hit a roadblock already before we started. The first node also sees your IP, but not the contents of your request.
What are some other problems with TOR? Well, a lot of websites simply block it, or otherwise try to make its usage inconvenient. Since the list of exit nodes is public, any website owner can easily do it. So you might be planning to "anonymize your browsing", but then realize it's simply unsuitable for everyday usage. Even more so if you intend to actually interact with the websites you're visiting - forums, imageboards, markets, file download websites, etc. all famously hate TOR. If push comes to shove, ISPs could very easily block all TOR traffic as well - in fact this has already happened in Venezuela for example - https://www.accessnow.org/venezuela-blocks-tor/ (archive) (MozArchive).
What about the so-called hidden services - exclusive to the TOR network? Well, most of them are defunct and it's hard to find one that actually works - and if you do, mostly you just see some scraps. In my country, I was only able to find ONE onion forum that I could actually connect to, and it didn't have very much activity. Their servers are also routinely raided (see Freedom Hosting) and their owners jailed.
There are many ways of identifying TOR users anyway - browser fingerprinting, stylometry, or even people sharing their personal data while on TOR. Operation Onymous (archive) (MozArchive) was very successful (though kind of overstated by the feds - the amount of seized sites were "only" 27 - here is a list). An already famous case of a guy sending a bomb threat using TOR can be read here: https://www.bestvpn.com/privacy-news/harvard-bomb-threat-student-caught-using-guerrilla-mail-tor/ (archive) (MozArchive). They got him because he was the only person using TOR on that particular network at the time. The FBI has even paid a university to deanonymize TOR users (archive), and that's how Silk Road 2.0's owner could be locked up. This is just what we know about - more attacks are surely in use or preparation.
TOR still relies on its encryption, and if that's ever broken - say goodbye to your anonymity, since all the traffic is stored for possible future decryption. Though the TOR network does use Perfect Forward Secrecy, which should ensure the security of the encryption keys (without a direct attack on your device) - cracking the actual ciphers is still a possibility:
However, forward secrecy cannot defend against a successful cryptanalysis of the underlying ciphers being used, since a cryptanalysis consists of finding a way to decrypt an encrypted message without the key, and forward secrecy only protects keys, not the ciphers themselves.
Quantum computing makes this likely, too. Another thing that's absolutely required for the security of TOR (that somehow no one is speaking about) are the nine trusted-by-default directory authorities. If a few of those are ever compromised (maybe that's already the case?) all of TOR's advantages go out the window. This issue has been analyzed in depth here.
Even the praised TOR Browser is not perfectly safe - for example, just using different buttons in your window manager can expose a different screen resolution (TBB version 8.5.3, newest as of writing). The first theme is Murrine, second - Default XHDPI, if you want to confirm.
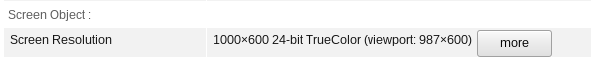
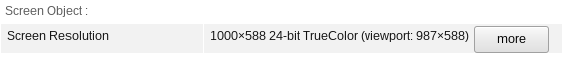
Of course, this alone is probably not enough to deanonymize you - but many more issues surely exist, waiting to be discovered. Put a few together and you might just find yourself exposed. Conclusion? TOR is not the panacea. Does that mean you shouldn't use it? No, of course. Use anything that's available to improve your privacy and anonymity - just realize it's not a magic spell, and does not strike at the core of the botnet.
UPDATE November 2024: another attack on TOR has recently dropped (archive) (MozArchive). It's quite creative, and it's summarized adequately in this one quote:
Could someone be deliberately trying to induce abuse complaints on Tor network participants to take down parts of the network (or disincetivize running internal nodes, which are key for the network’s health)?
The answer is yes:
This spoofing “attack” actually started on other types of nodes before migrating to relays, and those other nodes were hit with a much larger volume of spoofed connections, leading to them actually getting temporarily taken down in some cases!
Of course, this doesn't deanonymize anyone directly, but if people stop running nodes because of abuse reports (which is what I'd assume happens in a significant number of cases), it would decrease the anonymity for every TOR user.
You, too, can probably make your friend’s hosting provider (with their consent, of course) shut down their server and cancel their hosting contract by getting them flooded with well-meaning but confused abuse complaints.
Yes, you could. It always comes down to who owns the infrastructure, and who decides the "rules" according to which it runs. That's why we can't win this "war" by installing some type of software on our computers (alone). We need our own server spaces, our own ISPs, ones that keep no logs and ideally require no "contracts" to sign up for. Alternatively, to bypass the ISPs completely. Anything else is a mirage that's destined to disappear anytime an attack like this happens.
Inventing more darknets doesn't do anything
I don't care whether it's i2p or nym. I don't care how advanced they seem at first - weaknesses will be found eventually, like they were for TOR. They all rely on encryption that will be broken eventually. And they are all going through the enemy's networks. A meshnet has a too high barrier for entry (both skills and cost), and doesn't protect against states who have decided that selling meshnet devices will be banned, or the ones that have access to CCTV AI to detect who's using them, the ones who can compromise hardware at the production level (archive) (MozArchive) - Behind the scenes, BAC was secretly producing modified pagers containing the powerful explosive PETN, specifically targeting Hezbollah, reported The New York Times.
, the ones who can put an Alexa in your apartment by default (archive) (MozArchive) to hear what you're doing at all times, the ones who can delete you from existence by zeroing your bank account or throwing you into prison or doing any of the myriad of things that having access to the physical infrastructure lets them. Do you not see now how it all comes down to the physical infrastructure?
The core of internet surveillance
To derive benefit from the Internet's most popular services (like Facebook, Twitter, IM, website hosting), you have to deal with their terrible terms of service and privacy policies. Not only that, but any packet you send or receive is physically going through networks that you don't control. ISPs can watch, modify and block them any way they want - and they are subject to government whims as well. Encryption is at best a temporary non-solution, as explained in the TOR section (they could block all encrypted messages easily for example - by comparing them to known languages. If it's not found in any known language, the packet is trashed. Blocking HTTPs? What was it - port 443? Boom and done). Maybe some smart 'hackers' would learn to bypass these blocks, but in the end, we'd be fighting a battle we're sure to lose. Eventually we're going to have to face the fact that...